PRIMARY CATEGORY → PENTESTING
Notice
Be aware that this note is created to store all documentation which has not yet been assigned to a specific note or topic within the Pentesting section
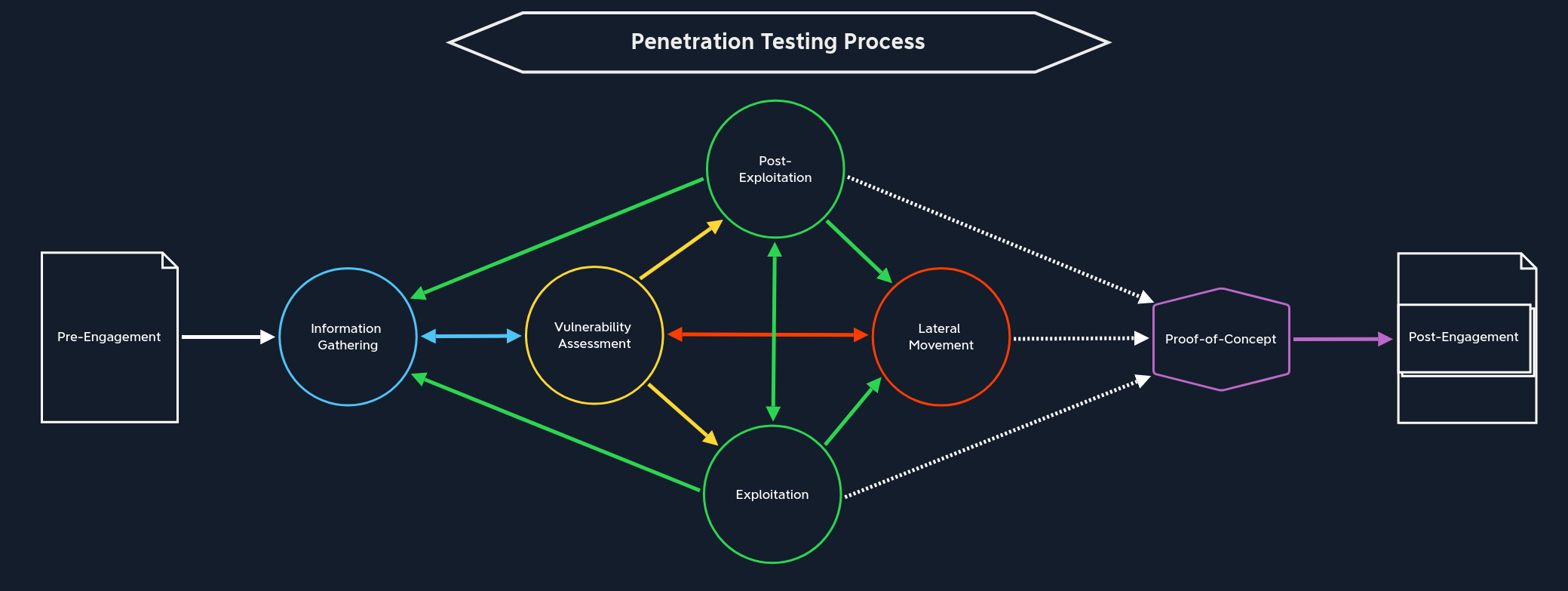
Penetration Testing Process
Privilege Escalation
Checklist
Hacktricks
PayloadAllTheThings
Enumeration Scripts
Kernel Exploitation
To check the Kernel Version in the Target System →
uname -rVulnerable Software
Check all installed software. It may has vulnerable/unpatched versions
- Linux
dpkg -l- Windows →
C:\Program FilesandC:\Program Files (x86)
User Privileges
- Sudo → Check sudo Privileges for the current user
sudo -l- SUID Binaries
find / -perm 4000 -type f 2> /dev/null
find / -user root -perm 4000 -type f 2> /dev/null # Only Root as EUIDLOLBAS - Windows Applications related to PE
Cron Jobs ~ Sheduled Tasks
Check Write Permissions over These directories
/etc/crontab
/etc/cron.d
/var/spool/cron/crontabs/root
SSH Keys
Check Read/Write Permissions over the .ssh Directory
- Read Perms → Copy the
id_rsacontent and login with that Private key via SSH
cat /root/.ssh/id_rsanvim ./id_rsa_target
chmod 600 !$
ssh -p<PORT> -i !$ ssh <USER>@<TARGET>- Write Perms → Create locally a key pair via
ssh-keygenand add the Public Key into the~/.ssh/authorized_keys. Then, login with the Private Key via SSH
ssh-keygen -b 4096 -t rsa -f ./key
cat !$.pub # Copy the Key.pub Contentnvim ~/.ssh/authorized_keys # Add the Key.pub Content within itssh -p<PORT> -i ./key <USER>@<TARGET>