PRIMARY CATEGORY → ZSH
In this Setup environment, all the following Shell Functions are declared in the custom.zsh script
Then, the custom.zsh script is sourced from the .zshrc file as follows →
# Custom Functions
if [[ -f /home/al3xbb/.config/zsh/src/custom.zsh ]] ; then
source /home/al3xbb/.config/zsh/src/custom.zsh
fiIMPORTANT
In the above code, an absolute path is used instead of the Tilde Expansion
~This is because the Root’s .zshrc file is a symbolic link to the non-privilege user’s .zshrc
Note that the
.config/zshdirectory only exists in/home/al3xbbbut not in/root
Custom.zsh Source File → See here
Terminal/Screen
Shell Functions related to the Terminal and Screen actions →
clearScreenAndScrollback
It clears the Screen Content and Scrollback Buffer through the C-l keybind
Function
clearScreenAndScrollback () { clear && printf '\e[3J' zle && zle .reset-prompt && zle -R }zle -N clearScreenAndScrollback bindkey '^L' clearScreenAndScrollback
More info here
Pentesting
Shell Functions related to the Pentesting Process →
Most of the functions are Non-POSIX-Compliant as ZSH is the Targeted Shell
mkt
It creates a Pentesting Folder Structure to store all documentation related to the target 🎯
Function
mkt() { local -- _dir= local -a -- _dirs=( evidence logs scans scope tools ) for _dir in "${_dirs[@]}" do mkdir -p -- "$_dir" [[ $_dir == "evidence" ]] && mkdir -p -- "$_dir"/{creds,data,screenshots} done }
IMPORTANT
Note that the above function is Non-POSIX Compliant due to Bash Specific Functionalities such as
local,[[ ]]shell keyword, Brace Expansion{ }or indexed arraysTherefore, It is not destined to POSIX Compliant shells like sh or dash
If POSIX Compliant is needed →
mkt() { _dir= _dirs="evidence logs scans scope tools" for _dir in $_dirs do mkdir -p -- "$_dir" [ "$_dir" = "evidence" ] && mkdir -p -- "$_dir"/creds \ "$_dir"/data \ "$_dir"/screenshot done }
extractPorts
This function mainly displays a Summary of the Target’s Open Ports
Furthermore, it copies the Open Ports to the System Clipboard
Function
extractPorts() { local -- _file=$1 _ip= _ipAddress= IFS=, \ _tmpFile=$( mktemp --quiet --suffix=.log --tmpdir=. ) local -a -- _ports=() trap 'rm --force "$_tmpFile"' RETURN [[ -s $_file ]] || { printf "\n[!] File must be a Nmap Grepable Format :)\n" 1>&2 return 1 } while IFS=$' ' read -r _ _ip do [[ $_ip =~ (^[[:digit:]]{1,3}(\.[[:digit:]]{1,3}){3}) ]] && { _ipAddress=${_ip%%[[:space:]]*} break } done < "$_file" while IFS= read -r _port do _ports+=( "$_port" ) done < <( grep --only-matching \ --perl-regexp \ '\s\K\d{1,5}(?=/open)' \ "$_file" ) cat << PORTS > "$_tmpFile" [+] Extracting information... [+] IP Address: $_ipAddress [+] Open Ports: ${_ports[*]} [+] Ports Copied to Clipboard PORTS command -V xclip &> /dev/null && xclip -sel clip < <( tr -d '\n' <<< "${_ports[*]}" ) command -V bat &> /dev/null && bat "$_tmpFile" return 0 }
IMPORTANT
An error related to the
trap 'COMMAND' RETURNline may occur when callling the functionIf this happens, simply replace the above line with
rm --force -- "$_tmpFile"at the end of the FunctionLikewise, instead of a function, the above code can be copied into a bash script as follows →
sudo nvim /usr/bin/extractPortschmod 777 !$Script Content
#!/usr/bin/env bash extractPorts() { FUNCTION_CONTENT } extractPorts "$@" || exit 99
validateIP
This function simply checks if the IP Address entered as an argument is valid
It is used by the setTarget function
Function
validateIP () { local _IP=$1 _octet= [[ $_IP =~ ^[0-9]+(\.[0-9]+){3}$ ]] || return 1 while read -rd '.' _octet do (( _octet > 255 )) && return 1 done <<< "$_IP". return 0 }
setTarget
It sets the Target’s IP Address and Hostname as one of the Polybar Bar’s Modules
This function prints the above data into the /home/al3xbb/.config/bin/target file
Then the Polybar Module carries out an action based on that File’s Content as follows →
- If Empty → “No target” as Polybar’s Bar Content
- If not Empty → File’s Content as the Polybar’s Bar Content, i.e. the IP Address and Hostame
Function
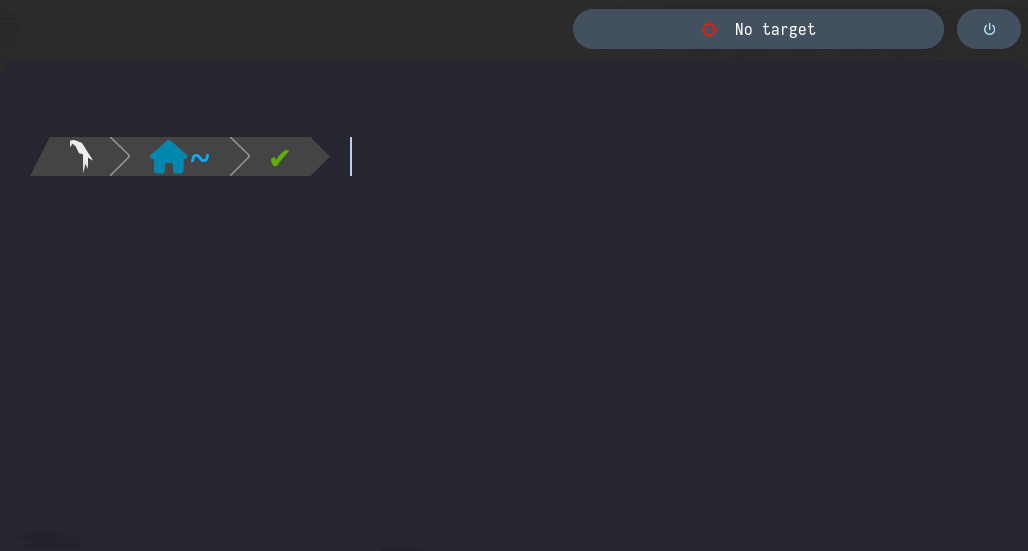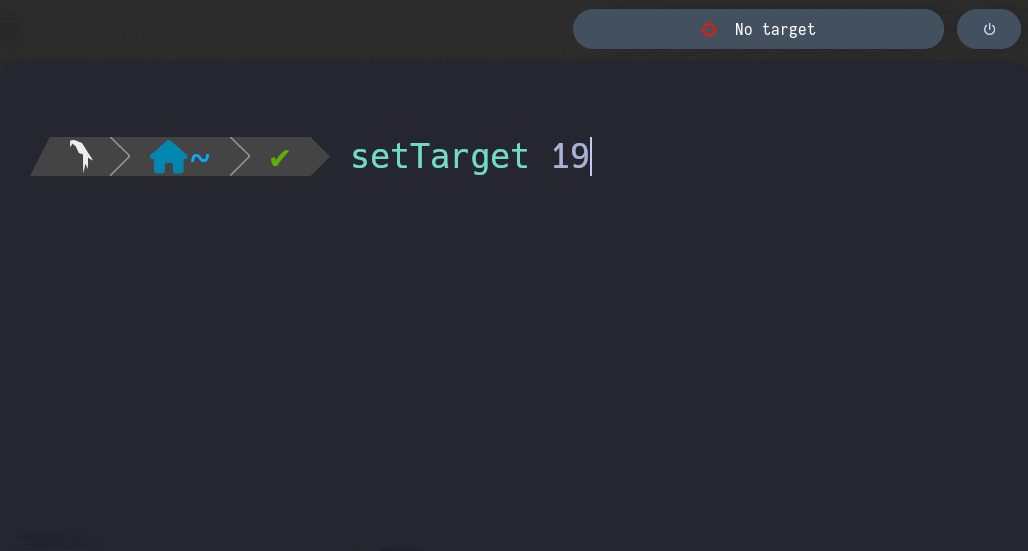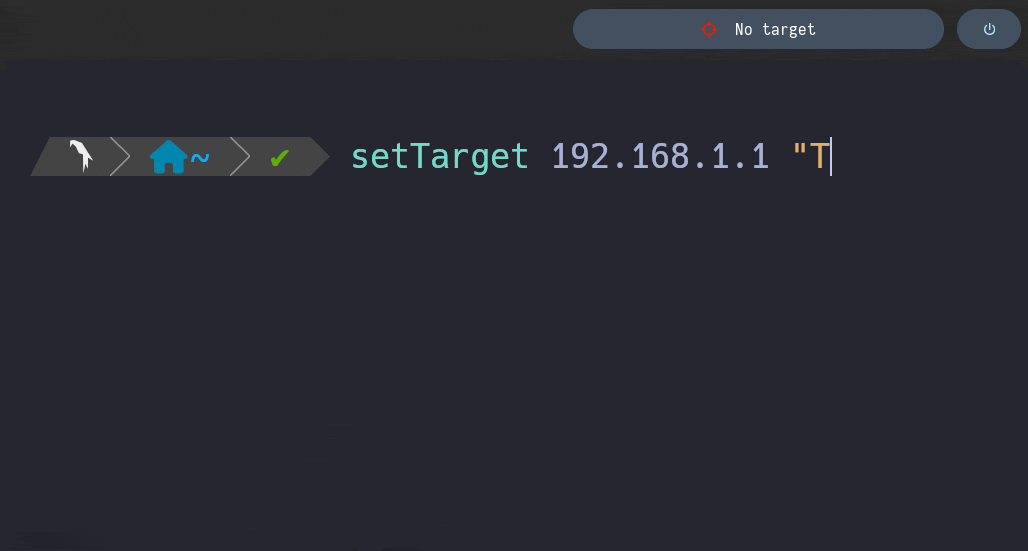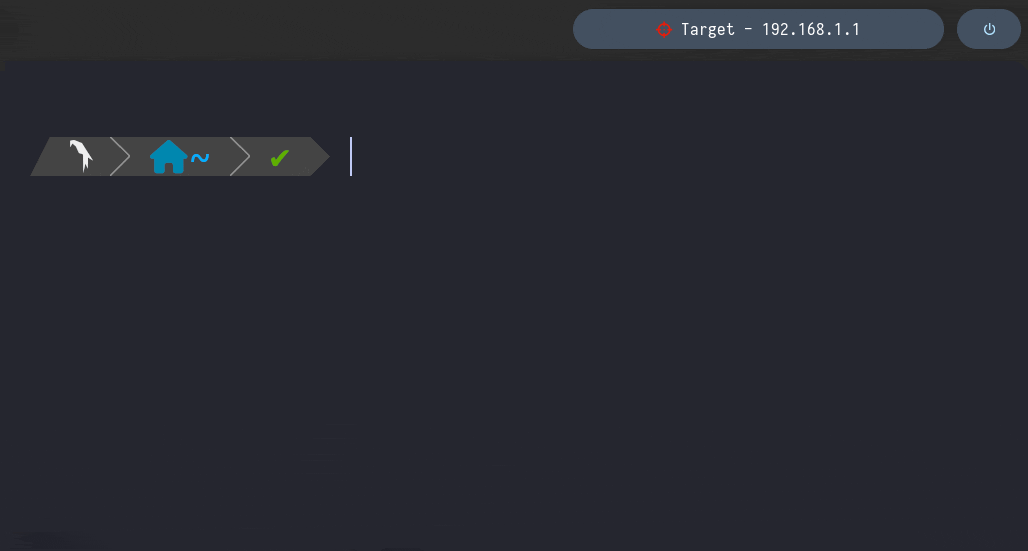
setTarget () { local -- _IP=$1 _machineName=$2 \ _targetFile=/home/al3xbb/.config/bin/target (( $# != 2 )) && { /bin/cat <<HELP 1>&2 [!] This function requires two arguments: IP Addresss and Machine Name Syntax: setTarget XXX.XXX.XXX.XXX "Machine Name" HELP return 1 } validateIP "$_IP" || { printf "\n%s\n" '[!] First arg must be a valid IP Address' 1>&2 return 1 } [[ -n $_IP && -n $_machineName ]] || { printf "\n%s\n" '[!] Args cannot be an empty string' 1>&2 return 1 } printf "%s:%s\n" "$_IP" "$_machineName" > "$_targetFile" }
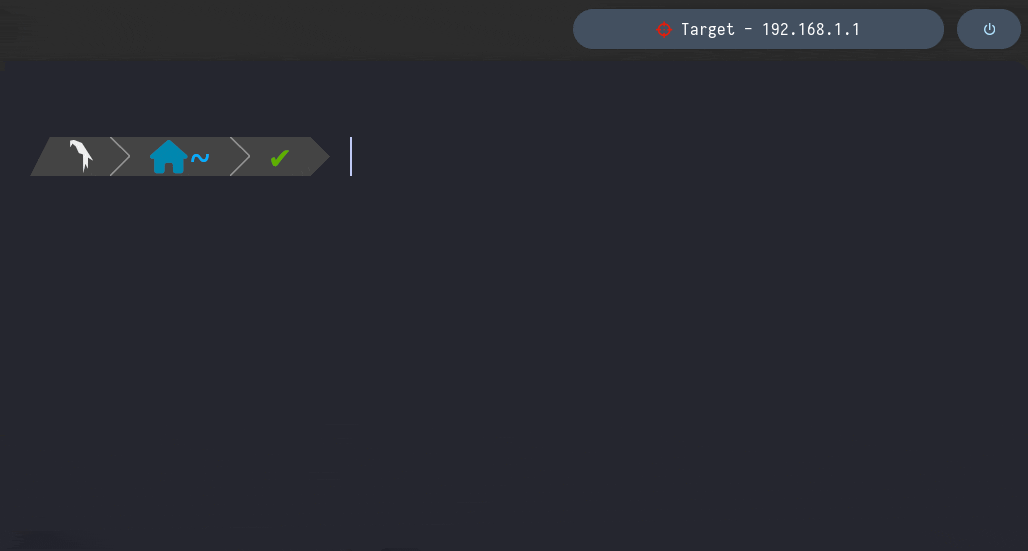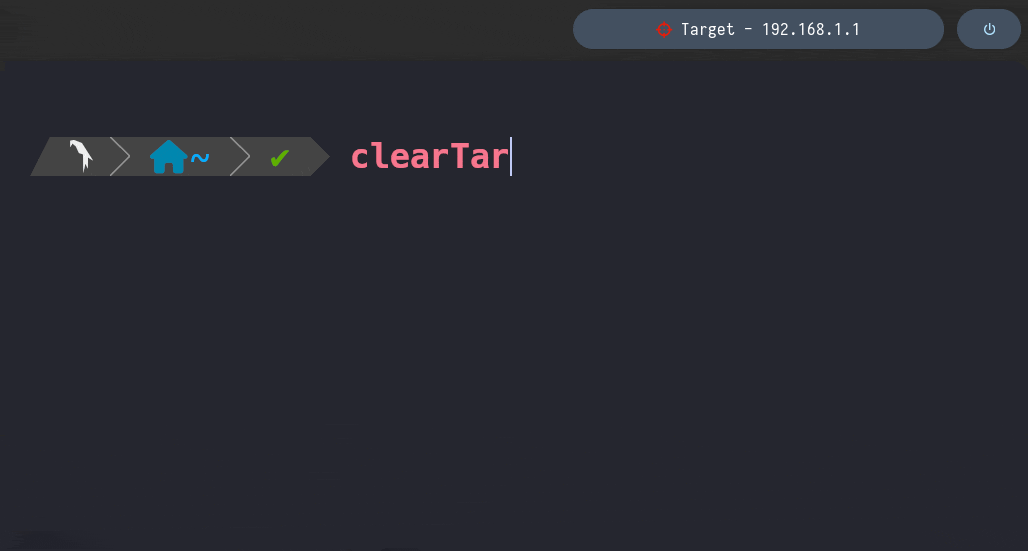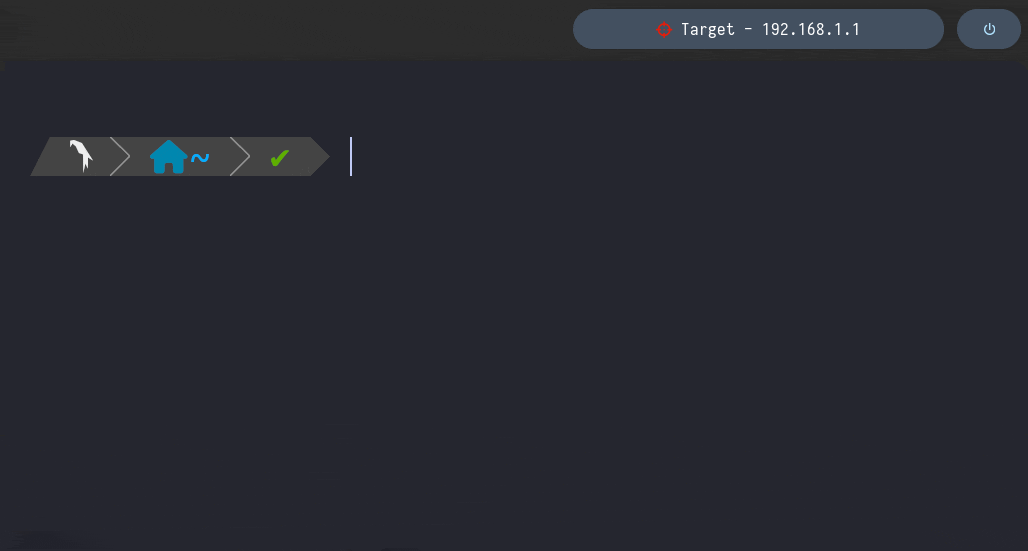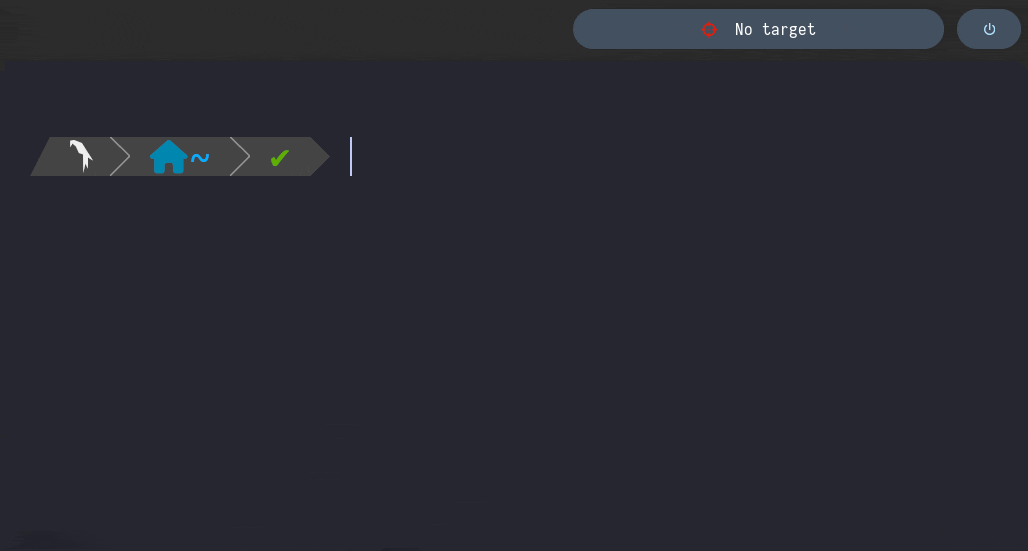
clearTarget
This functions empties the /home/al3xbb/.config/bin/target file
Therefore, as mentioned in the setTarget function, the Polybar Module sets “No Target” as Polybar Bar’s Content
Function
clearTarget () { local -- _targetFile=/home/al3xbb/.config/bin/target [[ -s $_targetFile ]] && : '' > "$_targetFile" || return 1 }